Tag: malware
Top Stories
Ukrainian Man Extradited to US for Alleged Cybercrime Ring
Raccoon Infostealer mastermind brought to justice.
The Antivirus Showdown: Bitdefender vs. Norton vs. TotalAV in 2024
Can't decide which antivirus champion reigns supreme? We dissect their strengths, weaknesses, and hidden jabs to help you choose your…
Unmasking RedEnergy: The New Hybrid Threat in Cybersecurity
The innovative cybersecurity group, Zscaler ThreatLabz, recently discovered a new malware variant—RedEnergy Stealer—that redefines ransomware threats by adopting a dual…
CISA Warns of Cyber Attacks on Ukraine
As Russia's military invasion of Ukraine officially marks its first anniversary, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) is…
Advanced Persistent Threats (APTs): Decoding the Invisible Enemy
Advanced Persistent Threats (APTs) are highly targeted and sophisticated cyberattacks that can cause significant damage to organizations. These attacks use…
GoDaddy Reveals Multi-Year Security Breach
Web hosting giant GoDaddy has recently confirmed a security breach that took place over several years. The breach allowed unauthorized…
CircleCI Reveals Malware Attack as the Cause of Recent Security Breach
DevOps platform CircleCI has announced that an malicious actor that successfully implanted malware on an internal engineer's laptop was responsible…
Exploiting Advanced Volatile Memory Analysis Challenges for Fun and Profit
Malware continues to advance in sophistication and prevalence. Well-engineered malware can obfuscate itself from the user, network, and even the…
An In-Depth Guide to Network Security
How much do you know about network security? Do you have a high-level understanding of how it works? Do you…
Behind The Scenes of a Malware Analysis
Every computer user understands the importance of cybersecurity in today’s world, and businesses must work hard to protect themselves against…
How Law Firms Can Strengthen Their Cybersecurity
As technology evolves, the threat of cyber attacks also rises. When a law firm faces cyber attacks, it can lead…
DirtyMoe Malware Botnet Returns
DirtyMoe is a malware botnet that has been around since at least 2016, but its most recent version includes some…
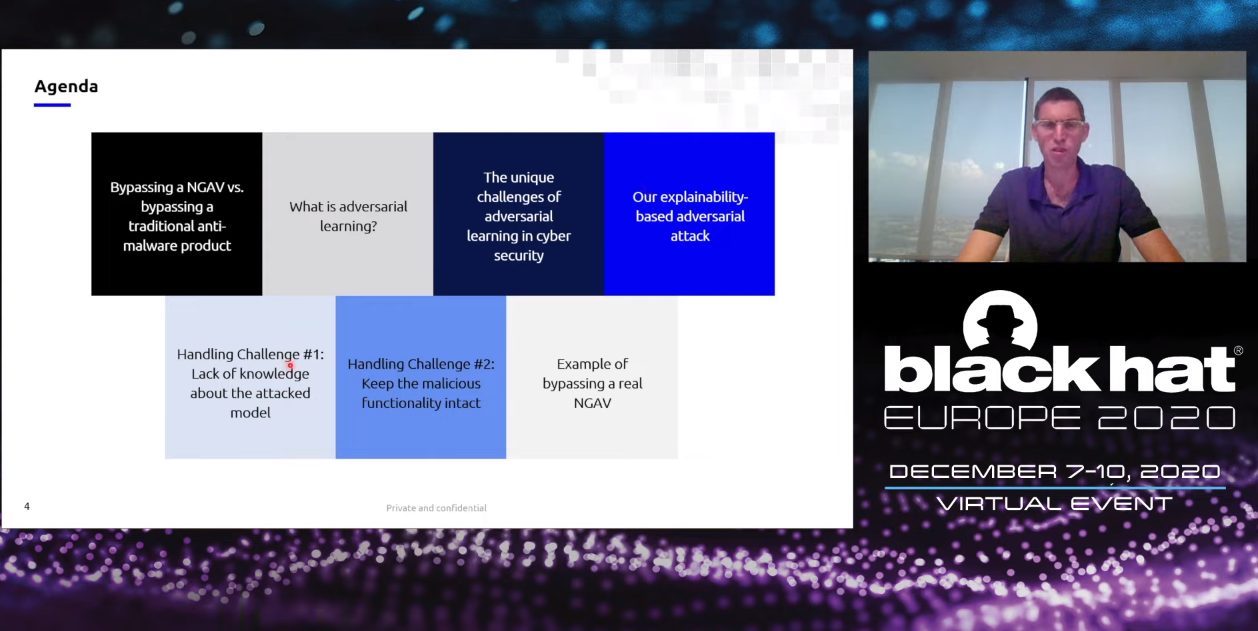
Bypassing NGAV by Shai Meir and Ishai Rosenberg
In this talk, Shai Meir and Ishai Rosenberg demonstrate the first methodological approach to reverse engineer a NGAV model and…
0-Day Vulnerability – How it Works?
A 0day (Zero-day) vulnerability is a software security flaw that is known to the software vendor but doesn’t have a…
Attackers finding new ways to exploit and bypass Office 365 defenses
Over the six-month period from March to August 2020, over 925,000 malicious emails managed to bypass Office 365 defenses and…
Blackout in Johannesburg Caused by Ransomware
A ransomware infection has been reported on the systems of one of South Africa’s leading power suppliers, specifically in the…
North Korean hacker officially charged for the WannaCry attacks
Park Jin Hyok, North Korean hacker, who has officially been charged by the US Department of Justice for carrying out the WannaCry attacks, among other…
Banking Malware Uncovered After 5 Years
Security analysts at Kaspersky Labs have revealed another, complex malware that has been focusing on clients of a few Mexican…
Malware Hidden In Images Is Used By Hackers
Malware that utilizes Exchangeable Image File Format (EXIF) data to shroud its code has moved to another stage: GoogleUserContent locales,…
Nocturnal Stealer malware harvests sensitive info
Nocturnal Stealer malware is available for sale through Deep Web sources, for the low price of 25$. It steals 28…